 |
|
Please Whitelist This Site?
I know everyone hates ads. But please understand that I am providing premium content for free that takes hundreds of hours of time to research and write. I don't want to go to a pay-only model like some sites, but when more and more people block ads, I end up working for free. And I have a family to support, just like you. :)
If you like The TCP/IP Guide, please consider the download version. It's priced very economically and you can read all of it in a convenient format without ads.
If you want to use this site for free, I'd be grateful if you could add the site to the whitelist for Adblock. To do so, just open the Adblock menu and select "Disable on tcpipguide.com". Or go to the Tools menu and select "Adblock Plus Preferences...". Then click "Add Filter..." at the bottom, and add this string: "@@||tcpipguide.com^$document". Then just click OK.
Thanks for your understanding!
Sincerely, Charles Kozierok
Author and Publisher, The TCP/IP Guide
|
|
|

Custom Search
|
|
POP3 General Operation, Client/Server Communication and Session States
(Page 2 of 2)
Session States
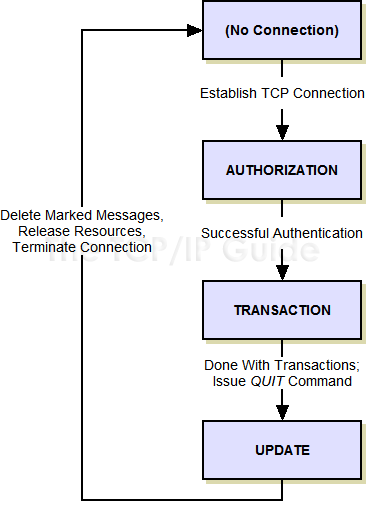
POP3 is described in terms of a finite state machine (FSM), with a session transitioning through three states during the course of its “lifetime”, as shown in Figure 306.
|
Before you get too intimidated, realize that unlike the FSMs of protocols like TCP, this one really is simple, because it is linear. The session goes through each state once and only once, in the following sequence:
- Authorization State:
The server provides a greeting to the client to indicate that it is
ready for commands. The client then provides authentication information
to allow access to the user's mailbox.
- Transaction State: The
client is allowed to perform various operations on the mailbox. These
include listing and retrieving messages, and marking retrieved messages
for deletion.
- Update State: When the
client is done with all of its tasks and issues the QUIT command,
the session enters this state automatically, where the server actually
deletes the messages marked for deletion in the Transaction state.
The session is then concluded and the TCP connection between the two
terminated.
Figure 306: Post Office Protocol (POP3) Finite State Machine
POP uses a finite state machine to describe its operation, but it is very simple because it is linear. Once a TCP connection is established between a POP3 client and POP3 server, the session proceeds through three states in sequence, after which the connection is terminated.
POP3 is designed so that only certain commands may be sent in each of these states. The next three topics describe the activities that take place in these three states, including the commands that are issued by the client in each.
|
|
| |||||||||||||||||||
Home - Table Of Contents - Contact Us
The TCP/IP Guide (http://www.TCPIPGuide.com)
Version 3.0 - Version Date: September 20, 2005
© Copyright 2001-2005 Charles M. Kozierok. All Rights Reserved.
Not responsible for any loss resulting from the use of this site.







 Note: I describe the concepts behind Finite State Machines in
Note: I describe the concepts behind Finite State Machines in  Key Concept: POP3 is a client/server protocol that is described using a simple linear sequence of states. A POP3 session begins with a POP3 client making a TCP connection to a POP3 server, at which point the session is in the Authorization state. After successful authentication, the session moves to the Transaction state, where the client can perform mail access transactions. When it is done, the client ends the session and the Update state is entered automatically, where cleanup functions are performed and the POP3 session ended.
Key Concept: POP3 is a client/server protocol that is described using a simple linear sequence of states. A POP3 session begins with a POP3 client making a TCP connection to a POP3 server, at which point the session is in the Authorization state. After successful authentication, the session moves to the Transaction state, where the client can perform mail access transactions. When it is done, the client ends the session and the Update state is entered automatically, where cleanup functions are performed and the POP3 session ended.