 |
|
Please Whitelist This Site?
I know everyone hates ads. But please understand that I am providing premium content for free that takes hundreds of hours of time to research and write. I don't want to go to a pay-only model like some sites, but when more and more people block ads, I end up working for free. And I have a family to support, just like you. :)
If you like The TCP/IP Guide, please consider the download version. It's priced very economically and you can read all of it in a convenient format without ads.
If you want to use this site for free, I'd be grateful if you could add the site to the whitelist for Adblock. To do so, just open the Adblock menu and select "Disable on tcpipguide.com". Or go to the Tools menu and select "Adblock Plus Preferences...". Then click "Add Filter..." at the bottom, and add this string: "@@||tcpipguide.com^$document". Then just click OK.
Thanks for your understanding!
Sincerely, Charles Kozierok
Author and Publisher, The TCP/IP Guide
|
|
|

Custom Search
|
|
POP3 Transaction State: Mail and Information Exchange Process and Commands
(Page 2 of 2)
Typical POP3 Mail Exchange Sequence
The Transaction state is relatively “unstructured” in that commands do not need to be issued in any particular order to meet the requirements of the standard. However, there is a natural progression to how a mailbox is retrieved, and that means the commands are usually used in the following way:
- The client issues a STAT command
to see the number of messages in the mailbox.
- The client issues a LIST command
and the server tells it the number of each message to be retrieved.
- The client issues a RETR command
to get the first message and if successful, marks it for deletion with
DELE. The client uses RETR/DELE for each successive message.
Figure 308: Post Office Protocol (POP3) Mail Exchange Process
This diagram shows the typical exchange of commands and replies employed by a POP3 client to retrieve e-mail from a POP3 server. The STAT command is used to get mailbox statistics, followed by the LIST command to obtain a list of message numbers. Each message in turn is then retrieved using RETR and marked for deletion by DELE. (Messages are not actually deleted until the Update state is entered.)
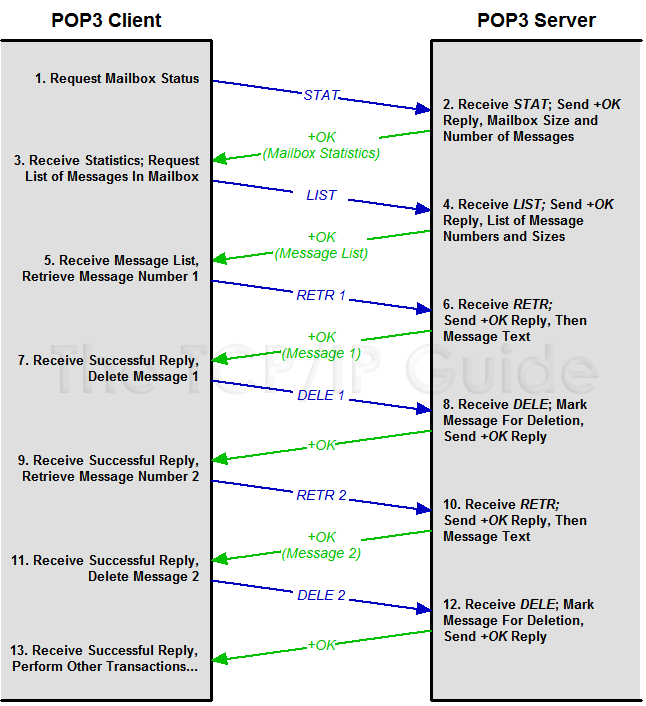
Table 258 and Figure 308 show a sample access sequence for a mailbox containing two messages that are a total of 574 bytes; the client's commands are highlighted and the server's responses are in italics.
STAT |
The exact message sent in reply to each command is server-dependent; some just say “+OK” while others provide more descriptive text as I have done here for the responses to the DELE command.
In some cases, a POP3 client may be configured to not delete messages after retrieving them. This is useful, for example, when Web-based access is being combined with a conventional e-mail client program.
|
|
| |||||||||||||||||||
Home - Table Of Contents - Contact Us
The TCP/IP Guide (http://www.TCPIPGuide.com)
Version 3.0 - Version Date: September 20, 2005
© Copyright 2001-2005 Charles M. Kozierok. All Rights Reserved.
Not responsible for any loss resulting from the use of this site.







 Key Concept: After successful authorization, the POP3 session transitions to the Transaction state, where the client actually accesses e-mail messages on the server. The client normally begins by first retrieving statistics about the mailbox from the server, and obtaining a list of the messages in the mailbox. The client then retrieving each message one at a time, marking each retrieved message for deletion on the server.
Key Concept: After successful authorization, the POP3 session transitions to the Transaction state, where the client actually accesses e-mail messages on the server. The client normally begins by first retrieving statistics about the mailbox from the server, and obtaining a list of the messages in the mailbox. The client then retrieving each message one at a time, marking each retrieved message for deletion on the server.