|
|
Please Whitelist This Site?
I know everyone hates ads. But please understand that I am providing premium content for free that takes hundreds of hours of time to research and write. I don't want to go to a pay-only model like some sites, but when more and more people block ads, I end up working for free. And I have a family to support, just like you. :)
If you like The TCP/IP Guide, please consider the download version. It's priced very economically and you can read all of it in a convenient format without ads.
If you want to use this site for free, I'd be grateful if you could add the site to the whitelist for Adblock. To do so, just open the Adblock menu and select "Disable on tcpipguide.com". Or go to the Tools menu and select "Adblock Plus Preferences...". Then click "Add Filter..." at the bottom, and add this string: "@@||tcpipguide.com^$document". Then just click OK.
Thanks for your understanding!
Sincerely, Charles Kozierok
Author and Publisher, The TCP/IP Guide
|
|
|

Custom Search
|
|
IPSec Architectures and Implementation Methods
(Page 2 of 3)
IPSec Architectures
Three different architectures are defined that describe methods for how to get IPSec into the TCP/IP protocol stack.
Under ideal circumstances, we would integrate IPSec's protocols and capabilities directly into IP itself. This is the most elegant solution, as it allows all IPSec security modes and capabilities to be provided just as easily as regular IP. No extra hardware or architectural layers are needed.
IPv6 was designed to support IPSec, making this a viable option for hosts or routers. With IPv4, integration would require making changes to the IP implementation on each device, which is often impractical (to say the least!)
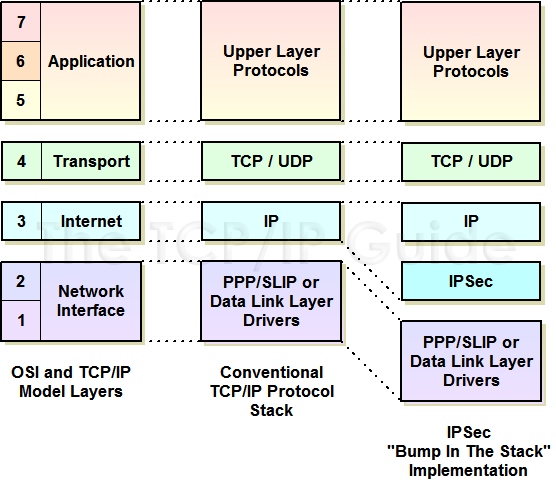
In this technique, IPSec is made a separate architectural layer between IP and the data link layer; the cute name refers to the fact that IPSec is an extra element in the networking protocol stack, as you can see in Figure 117. IPSec intercepts IP datagrams as they are passed down the protocol stack, processes them to provide security, and then passes them through to the data link layer.
The advantage of this technique is that IPSec can be “retrofitted” to any IP device, since the IPSec functionality is separate from IP. The disadvantage is that there is duplication of effort compared to the integrated architecture. BITS is generally used for IPv4 hosts.
|
|
| |||||||||||||||||||
Home - Table Of Contents - Contact Us
The TCP/IP Guide (http://www.TCPIPGuide.com)
Version 3.0 - Version Date: September 20, 2005
© Copyright 2001-2005 Charles M. Kozierok. All Rights Reserved.
Not responsible for any loss resulting from the use of this site.