 |
|
Please Whitelist This Site?
I know everyone hates ads. But please understand that I am providing premium content for free that takes hundreds of hours of time to research and write. I don't want to go to a pay-only model like some sites, but when more and more people block ads, I end up working for free. And I have a family to support, just like you. :)
If you like The TCP/IP Guide, please consider the download version. It's priced very economically and you can read all of it in a convenient format without ads.
If you want to use this site for free, I'd be grateful if you could add the site to the whitelist for Adblock. To do so, just open the Adblock menu and select "Disable on tcpipguide.com". Or go to the Tools menu and select "Adblock Plus Preferences...". Then click "Add Filter..." at the bottom, and add this string: "@@||tcpipguide.com^$document". Then just click OK.
Thanks for your understanding!
Sincerely, Charles Kozierok
Author and Publisher, The TCP/IP Guide
|
|
|

Custom Search
|
|
IP Variable Length Subnet Masking (VLSM)
(Page 3 of 3)
An Example: Multiple-Level Subnetting Using VLSM
VLSM subnetting is done the same way as regular subnetting; it is just more complex because of the extra levels of subnetting hierarchy. You do an initial subnetting of the network into large subnets, and then further break down one or more of the subnets as required. You add bits to the subnet mask for each of the "sub-subnets" and "sub-sub-subnets" to reflect their smaller size. In VLSM, the slash notation of classless addressing is commonly used instead of binary subnet masks—VLSM is very much like CIDR in how it works—so that's what I will use.
|
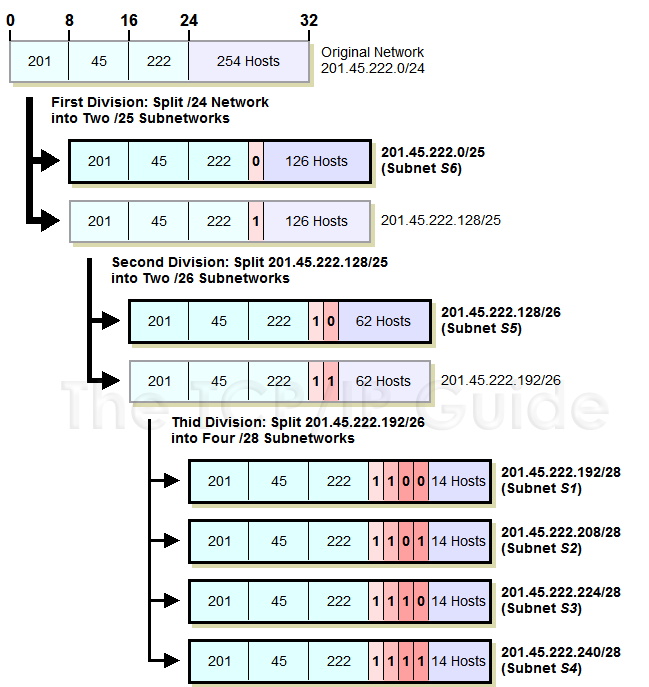
Let's take our example above again and see how we can make everything fit using VLSM. We start with our Class C network, 201.45.222.0/24. We then do three subnettings as follows (see Figure 72 for an illustration of the process):
- We first do an initial subnetting by
using one bit for the subnet ID, leaving us 7 bits for the host ID.
This gives us two subnets: 201.45.222.0/25 and 201.45.222.128/25. Each
of these can have a maximum of 126 hosts. We set aside the first of
these for subnet S6 and its 100 hosts.
- We take the second subnet, 201.45.222.128/25,
and subnet it further into two sub-subnets. We do this by taking one
bit from the 7 bits left in the host ID. This gives us the sub-subnets
201.45.222.128/26 and 201.45.222.192/26, each of which can have 62 hosts.
We set aside the first of these for subnet S5 and its 50 hosts.
- We take the second sub-subnet, 201.45.222.192/26,
and subnet it further into four sub-sub-subnets. We take 2 bits from
the 6 that are left in the host ID. This gives us four sub-sub-subnets
that each can have a maximum of 14 hosts. These are used for S1, S2,
S3 and S4.
Figure 72: Variable Length Subnet Masking (VLSM) Example
This diagram illustrates the example described in the text, of a Class C (/24) network divided using three hierarchical levels. It is first divided into two subnets; one subnet is divided into two sub-subnets; and one sub-subnet is divided into four sub-sub-subnets. The resulting six subnets are shown with thick black borders, and have a maximum capacity of 126, 62, 14, 14, 14 and 14 hosts.
Okay, I did get to pick the numbers in this example so that they work out just perfectly, but you get the picture. VLSM greatly improves both the flexibility and the efficiency of subnetting. In order to use it, routers that support VLSM-capable routing protocols must be employed. VLSM also requires more care in how routing tables are constructed to ensure that there is no ambiguity in how to interpret an address in the network.
As I said before, VLSM is similar in concept to the way classless addressing and routing (CIDR) is performed. The difference between VLSM and CIDR is primarily one of focus. VLSM deals with subnets of a single network in a private organization. CIDR takes the concept we just saw in VLSM to the Internet as a whole, by changing how organizational networks are allocated by replacing the single-level “classful” hierarchy with a multiple-layer hierarchy.
|
| |||||||||||||||||||
Home - Table Of Contents - Contact Us
The TCP/IP Guide (http://www.TCPIPGuide.com)
Version 3.0 - Version Date: September 20, 2005
© Copyright 2001-2005 Charles M. Kozierok. All Rights Reserved.
Not responsible for any loss resulting from the use of this site.







 Note: Before proceeding to the VLSM example that follows, a suggestion: if you aren't feeling comfortable with how basic subnetting works, you probably want to read through
Note: Before proceeding to the VLSM example that follows, a suggestion: if you aren't feeling comfortable with how basic subnetting works, you probably want to read through